WireGuard
Overview
WireGuard® is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography. It aims to be considerably more performant than OpenVPN, and is generally regarded as the most secure, easiest to use, and simplest VPN solution for modern Linux distributions.
WireGuard may be optionally installed by the Quick Installer. Once this is done, you can manage both local and remote server settings, create a peer configuration and control the wg-quick service with RaspAP.
Securing your wireless network
RaspAP gives you two ways to create a secure WireGuard tunnel: 1) by uploading a .conf file from your VPN provider, or 2) by creating a manual configuration. Each method is described and demonstrated with a short video below.
File upload
This method may be used if you are using a commerical WireGuard VPN provider, a self-hosted or other remote WG server. In these cases, it's assumed you have an existing WireGuard .conf file and wish
to upload this to RaspAP.
Note
The term "server" is used here as a convenience. WireGuard does not make a distinction between client and server roles. Instead, each node is considered a "peer" in a WireGuard network.
To do this, select the Upload file option under Configuration Method, select a valid WireGuard configuration file and choose Save settings. If your .conf
file does not contain iptables PostUp or PostDown rules and you wish to route traffic through the active AP interface, select the Apply iptables rules for AP interface option before uploading your
configuration file.
Attention
For security reasons, your WireGuard .conf file must have a Linux MIME type of text/plain. Windows ignores MIME types, relying instead on extensions. To avoid errors, be sure your file has a text/plain MIME type embedded in it before uploading.
The complete process of creating a WireGuard configuration with Mullvad and activating it with RaspAP is demonstrated in the video below.
It should be noted that RaspAP has no affiliation whatsoever with Mullvad. In fact, Mullvad does not use affiliates or pay for reviews. Members of RaspAP's Insiders community have requested support for this VPN provider.
Starting WireGuard
RaspAP will handle uploading your .conf file and, optionally, applying any iptables rules. To enable the tunnel, choose Start WireGuard. The WireGuard protocol is extremely fast, so in most cases
your new public IPv4 address will be indicated almost immediately. Click or tap the icon to open a new window with details about your public IP.
Verifying client connections
If you have chosen to route traffic from the wg0 interface to the AP interface, you may verify that your clients are secured by the WireGuard VPN. Start by connecting a client to your AP while
WireGuard is enabled. Again, using Mullvad as an example, visit their connection check page on your client device. If the tunnel is working correctly, you should see
a result like the following:

If any of the above checks fail, enable WireGuard service logging in RaspAP and check the output. You may also consult your VPN provider's support.
IPv6 considerations
RaspAP currently handles routing of IPv4 traffic only. For this reason, WireGuard server connections and traffic tunneled on IPv6 are incompatible. The solution is to specify IPv4 in your WireGuard VPN provider's advanced options (Mullvad is shown below):

Alternatively, open your .conf file in a text editor and ensure that the Address and AllowedIPs settings use IPv4 addresses only, like so:
[Interface]
PrivateKey = ░░░░░░░░░░░░░░░░░░░░░░░░░
Address = 10.64.171.100/32
DNS = 193.138.218.74
[Peer]
PublicKey = /pS3lXg1jTJ7I58GD/s/4GNL2B0U8JNbjbH9Ddh0myw=
AllowedIPs = 0.0.0.0/0
Endpoint = 185.254.75.3:51820
When this is done, you are ready to upload your configuration to RaspAP.
Manual configuration
Alternatively, RaspAP gives you full control over creating a manual WireGuard configuration. This method is useful if you wish to secure your local wireless network—that is, between your device running RaspAP and the clients connected to it.
WireGuard requires a public and private keypair for each device you wish to have access to the VPN tunnel. RaspAP simplifies this process with a magic button associated with each public key input field. Simply click or tap this button to securely generate a cryptographic keypair for both the server and peer.
Several default values are provided for you as a starting point. These are intended to get a VPN tunnel up and running quickly. They may be modified to suit your needs.
After the keypairs are generated, simply choose Save settings followed by Start WireGuard.
The video walkthrough below illustrates the steps of configuring a WireGuard tunnel from start to finish.
Due to WireGuard’s design, both computers on either end of the VPN tunnel will need to have each other's public key. This is discussed below.
Note
For security reasons, the local (server) private key is not displayed in the UI. The peer private key is encoded in the QR code and available to download in the client.conf file.
If you wish to regenerate local or peer keypairs (or both), simply tap or click the magic button and choose Save settings. Alternatively, to remove a server or peer configuration entirely, disable the desired toggle and Save settings. This will delete the public/private keypair and the associated configuration.
Peer configuration
RaspAP processes the values in the WireGuard Settings and Peer tabs and creates two configurations for you: wg0.conf and client.conf.
The former is used to configure the local (server) side of the VPN tunnel. The latter peer configuration is generated as a QR code on the Peer tab. Clients such as mobile devices
may scan the QR code to transfer client.conf and import it into an associated WireGuard client application.
The peer endpoint address may take the form of an IP address, hostname, or Dynamic DNS (DDNS) URL with the remote UDP port (31820 is typical).
Note
For this release, a single peer configuration may be created. The ability to manage multiple peer configurations is on the project roadmap.
Your peer will need to have WireGuard installed as well. For installing WireGuard on other systems, please see Wireguard's website.
Tunneling traffic
RaspAP uses WireGuard's PostUp and PostDown firewall rules to forward traffic from the wg0 interface to your configured wireless interface.
In the example below, the default AP interface wlan0 is used:
iptables -A FORWARD -i wlan0 -o wg0 -j ACCEPT
iptables -A FORWARD -i wg0 -o wlan0 -m state --state RELATED,ESTABLISHED -j ACCEPT
iptables -t nat -A POSTROUTING -o wg0 -j MASQUERADE
These iptables rules are defined in WireGuard's default settings and may be modified if you wish.
Note
If your VPN server is behind a NAT, you will need to open a UDP port of your choosing (51820 is the default).
Kill switch
Experimental
In the event that the WireGuard tunnel accidentally goes down, unencrypted traffic may reveal your real IP address. To prevent this from happening, additional PostUp and PreDown rules may be
added to the firewall. Simply choose the Enable kill switch option when uploading your WireGuard configuration:
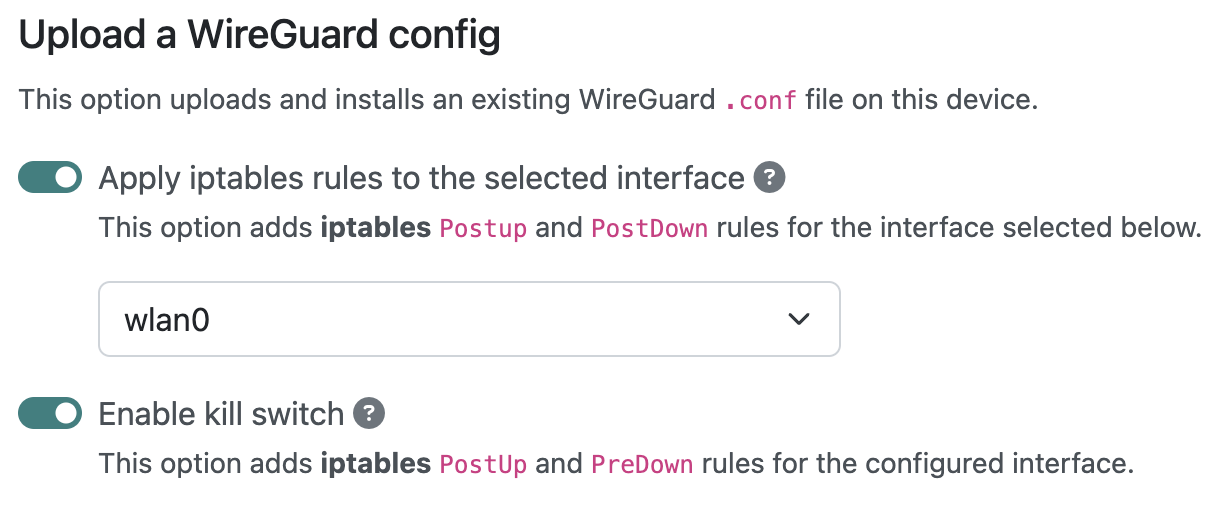
These rules are automatically appended to your configuration.
Note
Some VPN providers give you the option of adding these rules to their Linux configurations. Skip this option as RaspAP needs to add an exclusion rule for your AP interface.
Multiple configs
Experimental · Insiders only
RaspAP lets you manage multiple WireGuard configurations. This includes the ability to upload, activate and delete any number of valid wg .conf files. Select the Apply iptables rules for AP interface option when uploading your .conf file to automatically route traffic to connected peers on the AP interface.
Thereafter, switching between your saved configurations is done by simply activating the desired profile. Activating a profile will restart the wg-quick service automatically. Additionally, WireGuard service activity may be tracked on the Logging tab.
Low overhead
Due to its low overhead compared with OpenVPN, WireGuard is well-suited for applications where battery longevity is a concern. As described by its developer, WireGuard isn't a chatty protocol. For the most part, it only transmits data when a peer wishes to send packets. When it's not being asked to send packets, it stops sending packets until it is asked again.
As a result, your wireless adapter has a higher likelihood of being able to idle down, which leads to better battery life.
Troubleshooting
RaspAP provides a front end to WireGuard only; it makes no attempt to validate .conf files uploaded to your device. For this reason, the service may fail to start for a variety of reasons.
Tip
Drop to the shell and execute sudo systemctl start wg-quick@wg0. If WireGuard fails to start, expect no different from RaspAP.
In this event, use RaspAP's WireGuard service logging facility or execute sudo journalctl --identifier wg-quick. Scan the log for errors and consult the WireGuard documentation to ensure that your configuration is valid.
See also the FAQ section for WireGuard.
Discussions
Questions or comments about using WireGuard? Join the discussion here.